Transform commodity security services into differentiated technology offerings with autonomous drones
Deploy co-branded autonomous drone operations that scale client coverage, reduce false alarm costs by 70-85%, and enable profitable recurring revenue without proportional labor growth.
.avif)
Trusted by leading security service providers worldwide



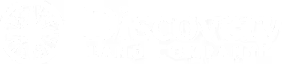
Transform commodity guard services into high-margin technology offerings
Scheduled patrols to AI-powered continuous monitoring
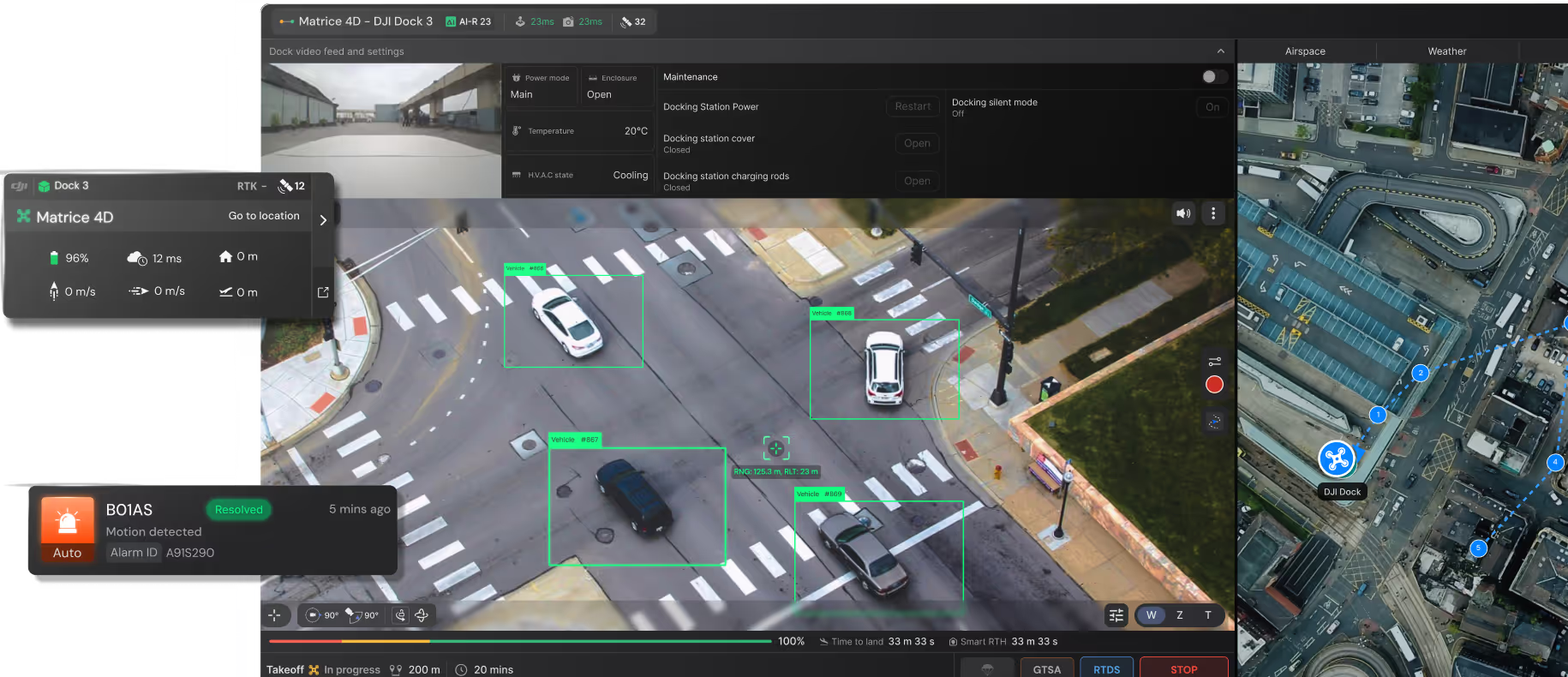
Automated missions execute 24/7 while FlytBase AI continuously analyzes video detecting people, vehicles, and threats—transforming drones from moving cameras into intelligent threat monitoring systems.
30-minute guard dispatch to 5-minute verification
Alarm-triggered drone launches collapse client response windows from 15-30 minute guard dispatch to under 5 minutes, enabling rapid threat assessment before incidents escalate.
Fixed cameras to flexible coverage
Aerial perspective eliminates infrastructure constraints of ground cameras. Cover large outdoor sites and remote perimeter zones without expensive fixed installations.
Manual patrol logs to automated documentation
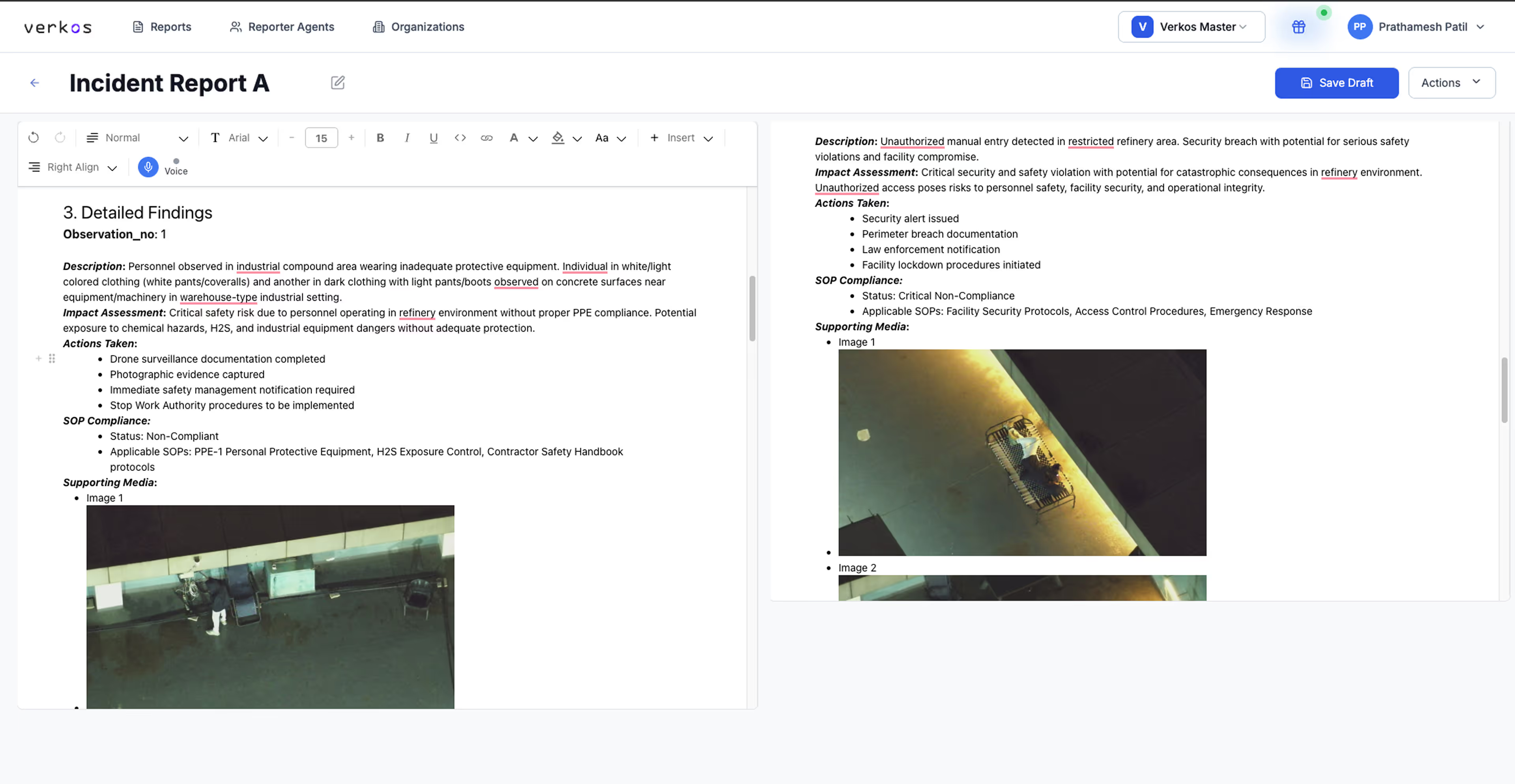
Every flight generates timestamped geo-referenced video records with complete audit trails, eliminating manual patrol documentation while providing defensible evidence for investigations and insurance.
FlytBase AI agents built for security operations
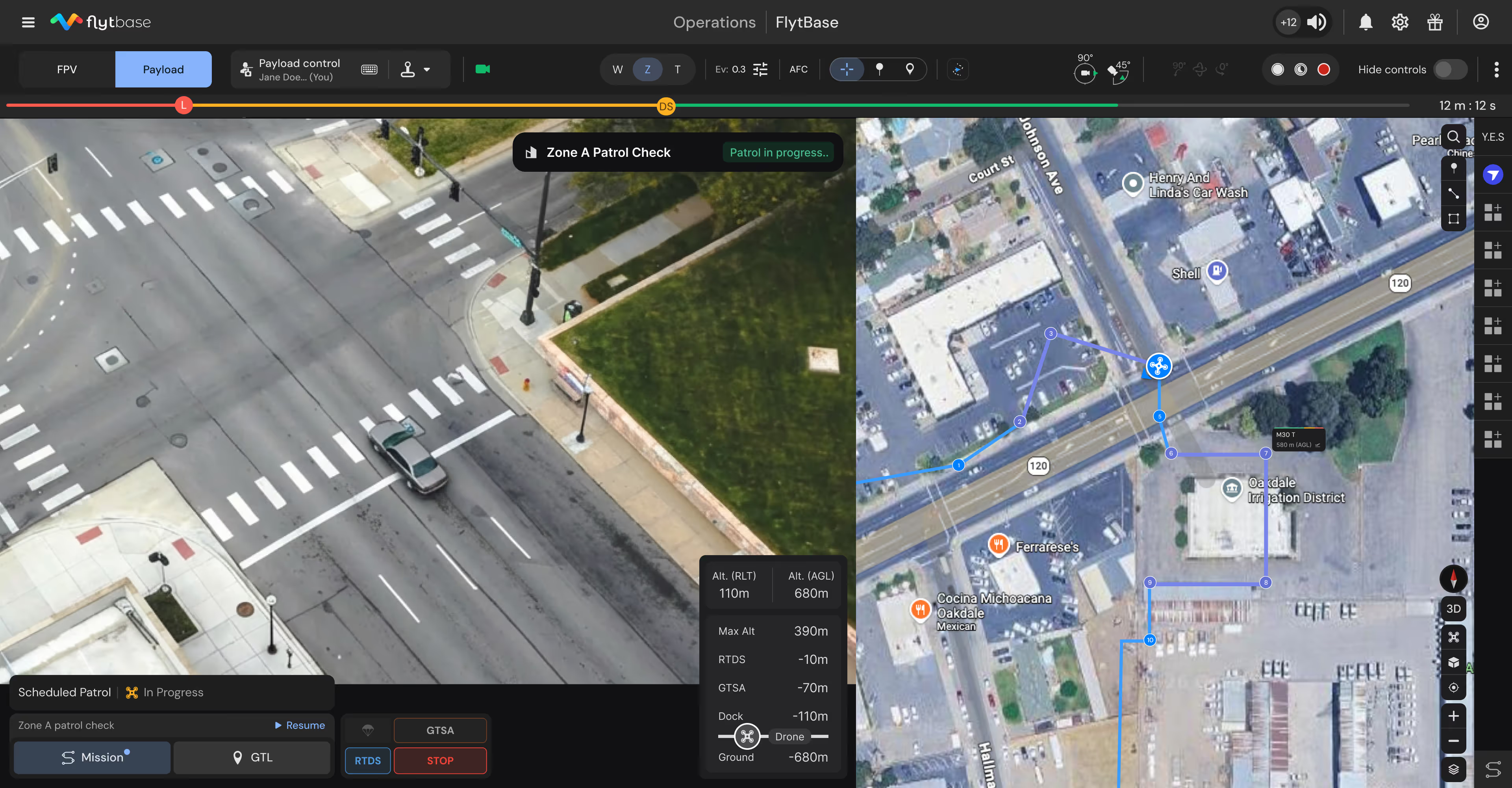
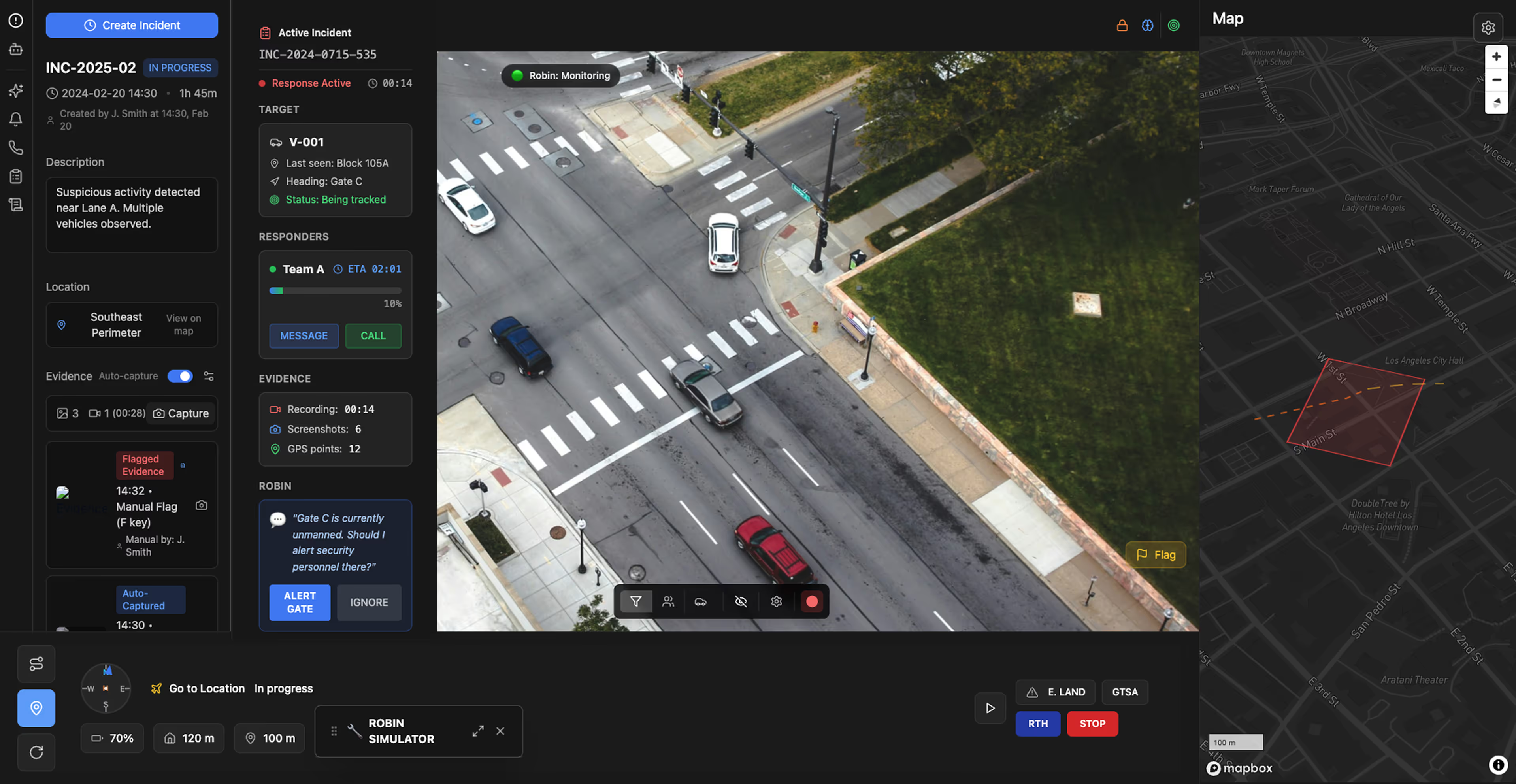
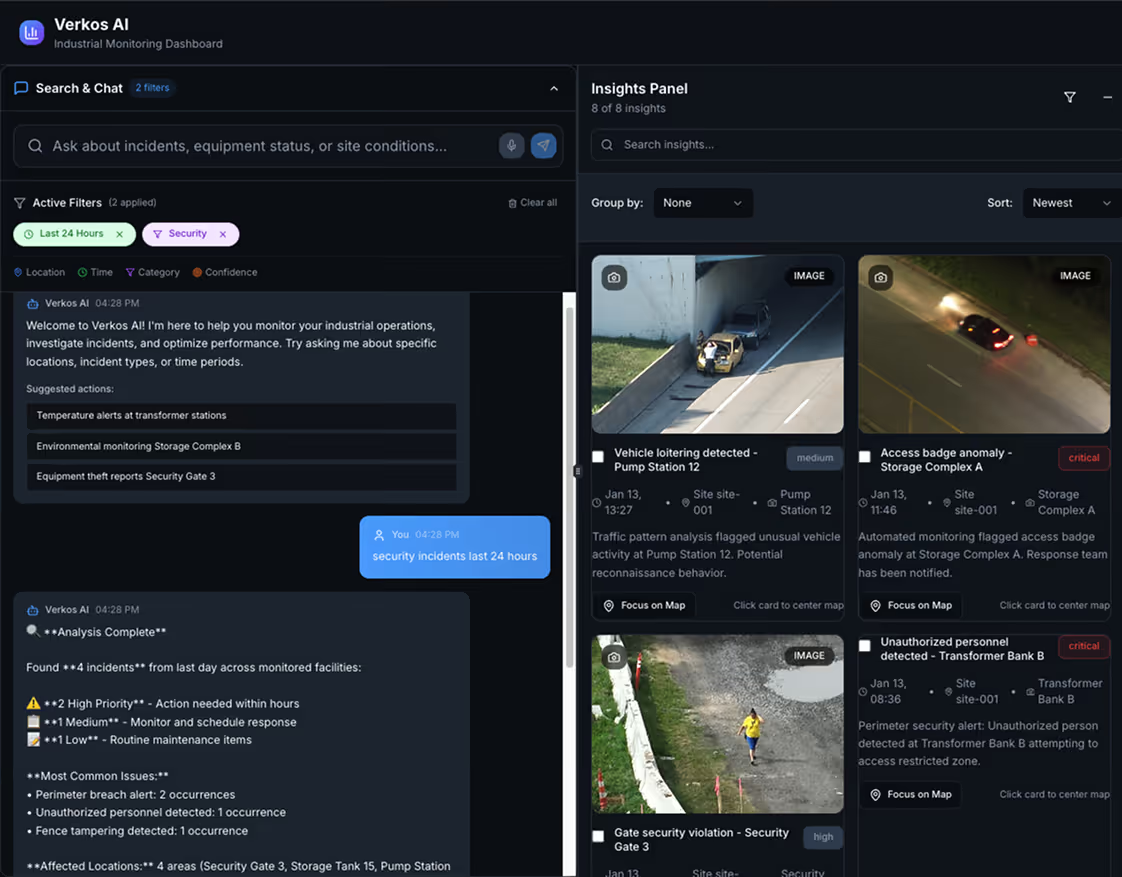
Assist security operations teams by automatically highlighting threats and filtering false alarms, reducing operator cognitive load across multiple client sites.

Person and vehicle detection
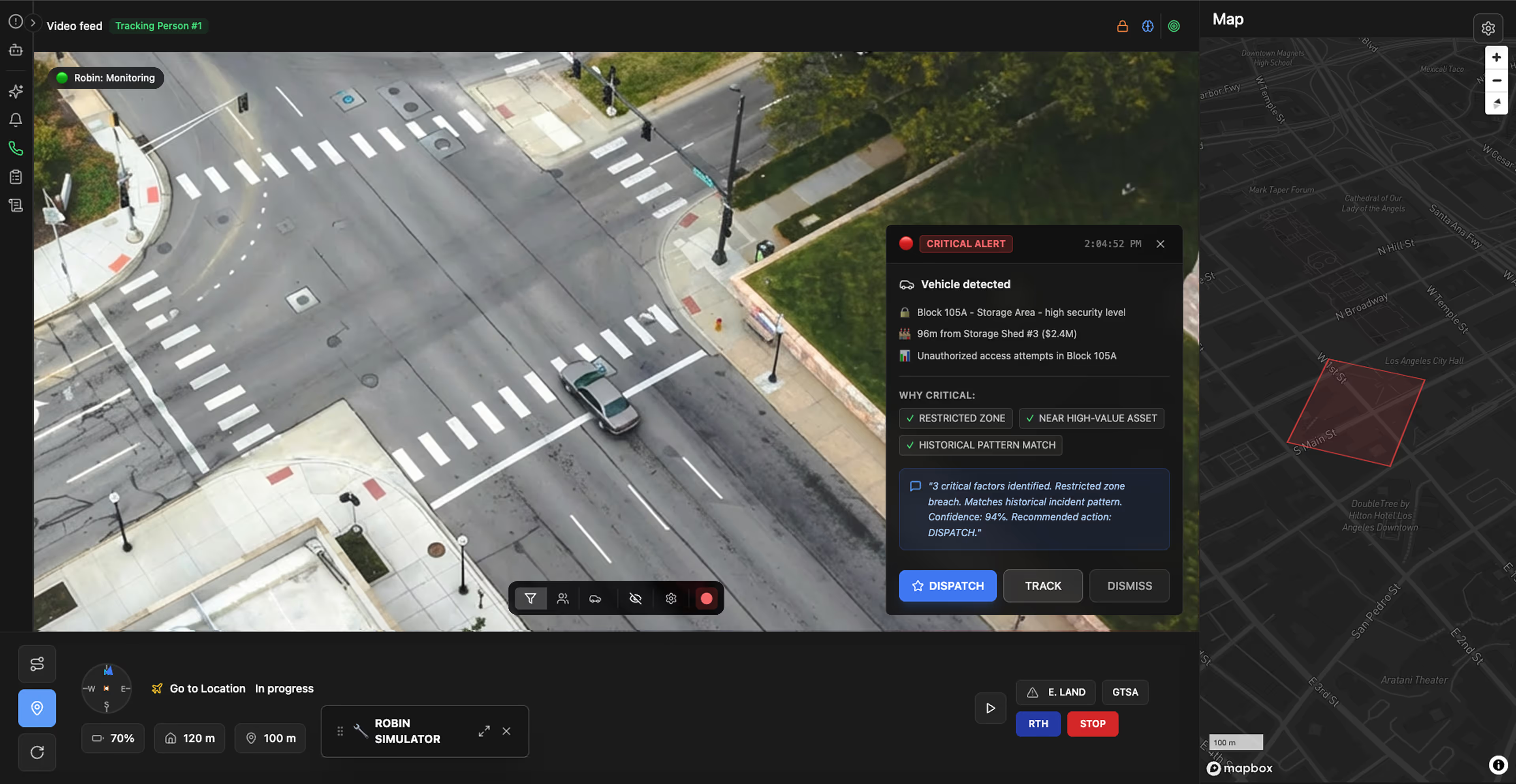
Identify people and vehicles in restricted zones, distinguishing authorized from unauthorized presence based on time and policy rules.

Zone violation alerts
Detect activity in restricted areas and perimeter breaches, filtering environmental false positives while prioritizing genuine security threats.

Thermal anomaly identification
Highlight heat signatures indicating unauthorized personnel, equipment faults, or fire risk during nighttime operations without visible lighting.

Unusual activity recognition
Flag deviations from normal operational patterns at each client site, distinguishing routine behavior from suspicious activity automatically.

Multi-site alert prioritization
Aggregate alerts across entire client portfolio, surfacing high-confidence threats with context enabling rapid operations center assessment decisions.
Historical evidence search
Query video archives by object type, zone, time, or asset to generate timestamped incident reports for client delivery.

Loitering detection
Identify vehicles or persons remaining in restricted areas beyond normal timeframes, highlighting potential staging activity for theft attempts.

After-hours presence flagging
Automatically alert on human or vehicle activity during client facility closed hours, reducing false alarms from scheduled maintenance.

Person and vehicle detection
Identify people and vehicles in restricted zones, distinguishing authorized from unauthorized presence based on time and policy rules.

Zone violation alerts
Detect activity in restricted areas and perimeter breaches, filtering environmental false positives while prioritizing genuine security threats.

Thermal anomaly identification
Highlight heat signatures indicating unauthorized personnel, equipment faults, or fire risk during nighttime operations without visible lighting.

Unusual activity recognition
Flag deviations from normal operational patterns at each client site, distinguishing routine behavior from suspicious activity automatically.

Multi-site alert prioritization
Aggregate alerts across entire client portfolio, surfacing high-confidence threats with context enabling rapid operations center assessment decisions.

Historical evidence search
Query video archives by object type, zone, time, or asset to generate timestamped incident reports for client delivery.

Loitering detection
Identify vehicles or persons remaining in restricted areas beyond normal timeframes, highlighting potential staging activity for theft attempts.

After-hours presence flagging
Automatically alert on human or vehicle activity during client facility closed hours, reducing false alarms from scheduled maintenance.
Designed for multi-client service delivery at scale
Automatically alert on human or vehicle activity during client facility closed hours, reducing false alarms from scheduled maintenance.
Drones and Docks
Support 24/7 autonomous operations using enterprise-grade drones and weatherproof docking stations across diverse client environments.

Payloads and accessories
Extend client service capabilities with thermal cameras, zoom lenses, spotlights, loudspeakers, and mission-specific payloads for different scenarios.

FlytBase drone autonomy platform
Orchestrate multi-site missions, AI-powered monitoring, client portal access, and compliance workflows through unified co-branded platform interface.
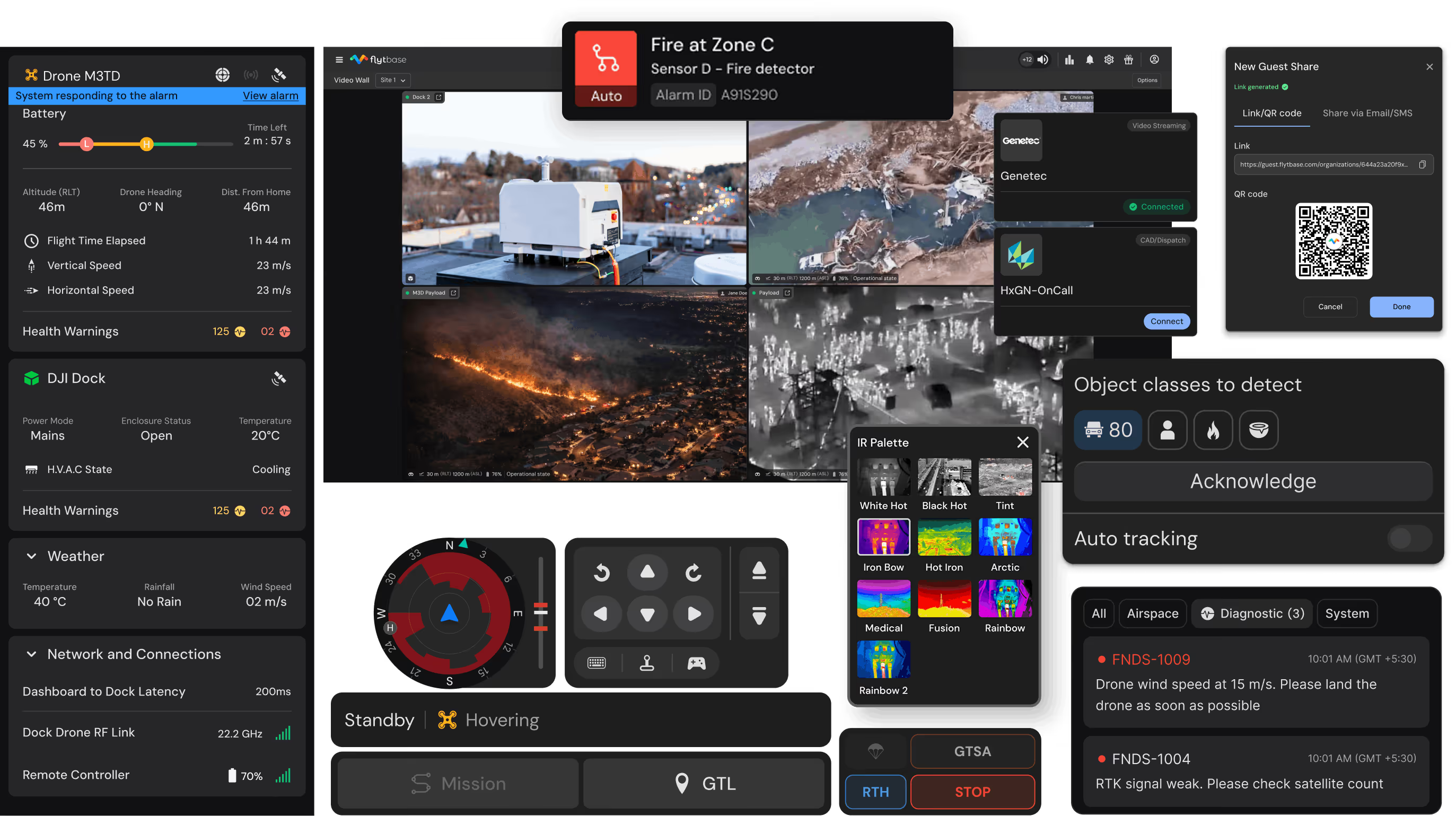
Apps and integrations
- Guard dispatch systemsAccess control and ticketingClient VMS platformsGIS toolsPerimeter sensors
Regulatory Approvals
One platform for enterprise-scale public safety drone autonomy
FlytBase provides the reliability intelligence and operational maturity required to run autonomous drone programs at scale across mission-critical public safety environments.
Co-branded platform
Launch drone services with your branding prominently featured, maintaining client relationships while leveraging enterprise technology.
Client portal included
Provide branded customer portals with live feeds, patrol history, and reports strengthening retention and upselling.

Local product and data sovereignty
Support in-country data residency, regional compliance needs, and local language requirements for multinational service operations.
AI-first architecture
Apply computer vision and threat detection designed specifically for security operations, not generic retrofitted capabilities.

Hardware agnostic flexibility
Support multiple drone manufacturers without platform lock-in, choosing optimal hardware for specific client missions.
Enterprise security compliance
Meet client requirements with SOC 2 compliance, encrypted transmission, role-based access, and flexible deployment models.