The Aerial Intelligence Layer for Physical Security
Build and scale drone-based security services using autonomous docked drones. Launch automatically on alarms, patrol large sites, stream live aerial intelligence to your command center, and deliver audit-ready evidence to clients. Works with your existing security systems and preferred hardware.






From Alarm Trigger to Verified Evidence In Four Automated Stages

AI Object Detection, Counting & Alerts
Combine any drone, docking station, payload, accessory & sensor of your choice. FlytNow supports it all.
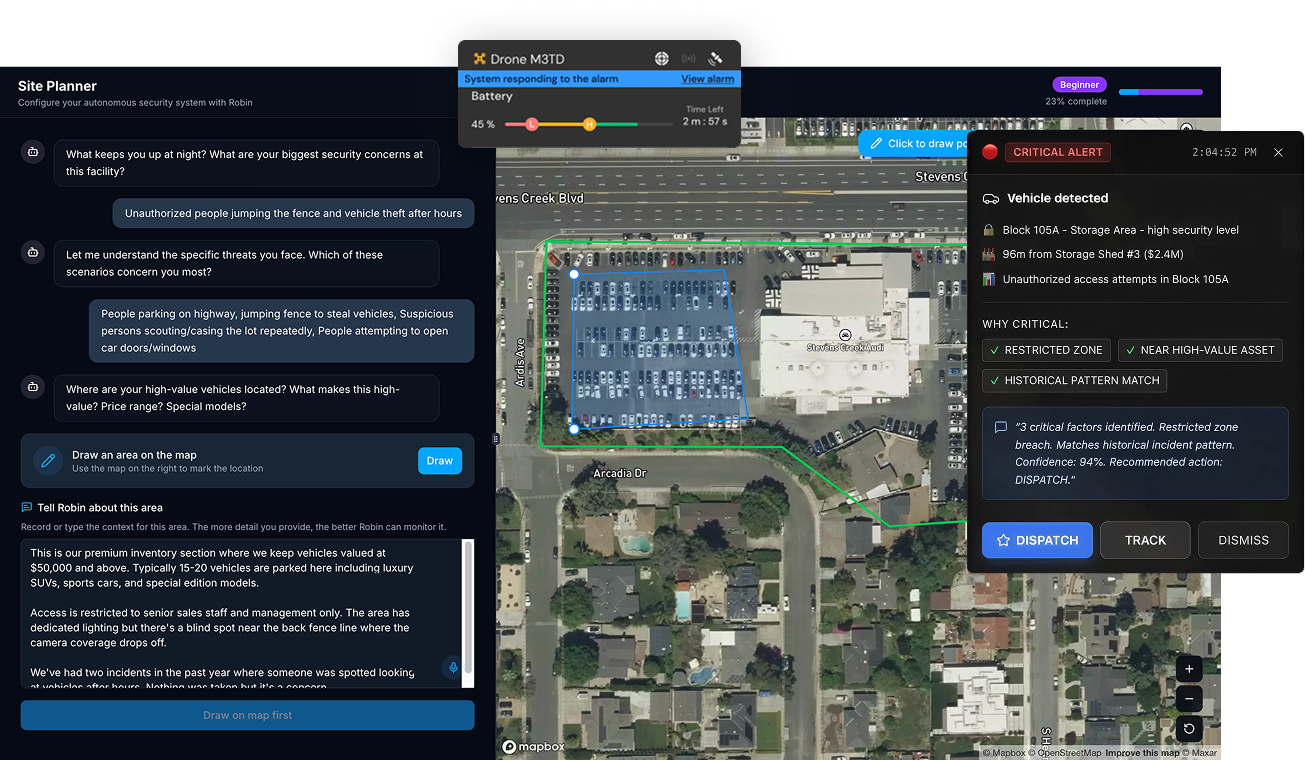
Eliminate manual monitoring of your drone feed with automated object detection, instant alerts via audio & on-screen notifs, and intelligent event logging. Identify threats or count assets with real-time AI-driven insights.
.webp)

Advanced Data Security
Gain full control of drone data with a secure sandboxed environment. Monitor network activity, enforce firewall protection, set allow/deny lists, track via interactive maps, and automate server blocking by region.

.webp)

AI Object Detection, Counting & Alerts
Combine any drone, docking station, payload, accessory & sensor of your choice. FlytNow supports it all.
Eliminate manual monitoring of your drone feed with automated object detection, instant alerts via audio & on-screen notifs, and intelligent event logging. Identify threats or count assets with real-time AI-driven insights.
.webp)

Live Streaming Engine
Combine any drone, docking station, payload, accessory & sensor of your choice. FlytNow supports it all.
Reduce video streaming costs by up to 5X with AI-R Edge. Process video locally eliminate cloud dependency and encode/decode on-site.
Securely stream the feed to your command center via private networks or VPN.
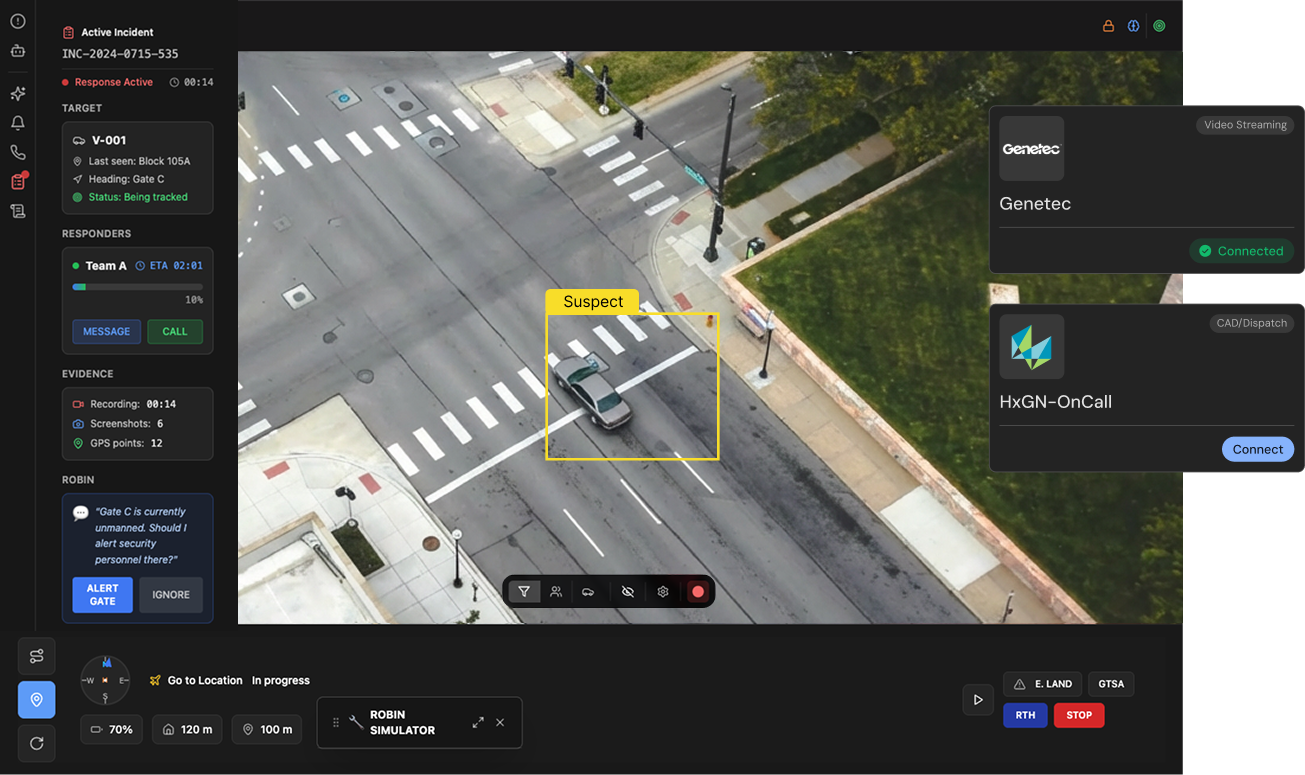
Automatic dispatch integration
Live response shared instantly
Incident coordination not just a feed
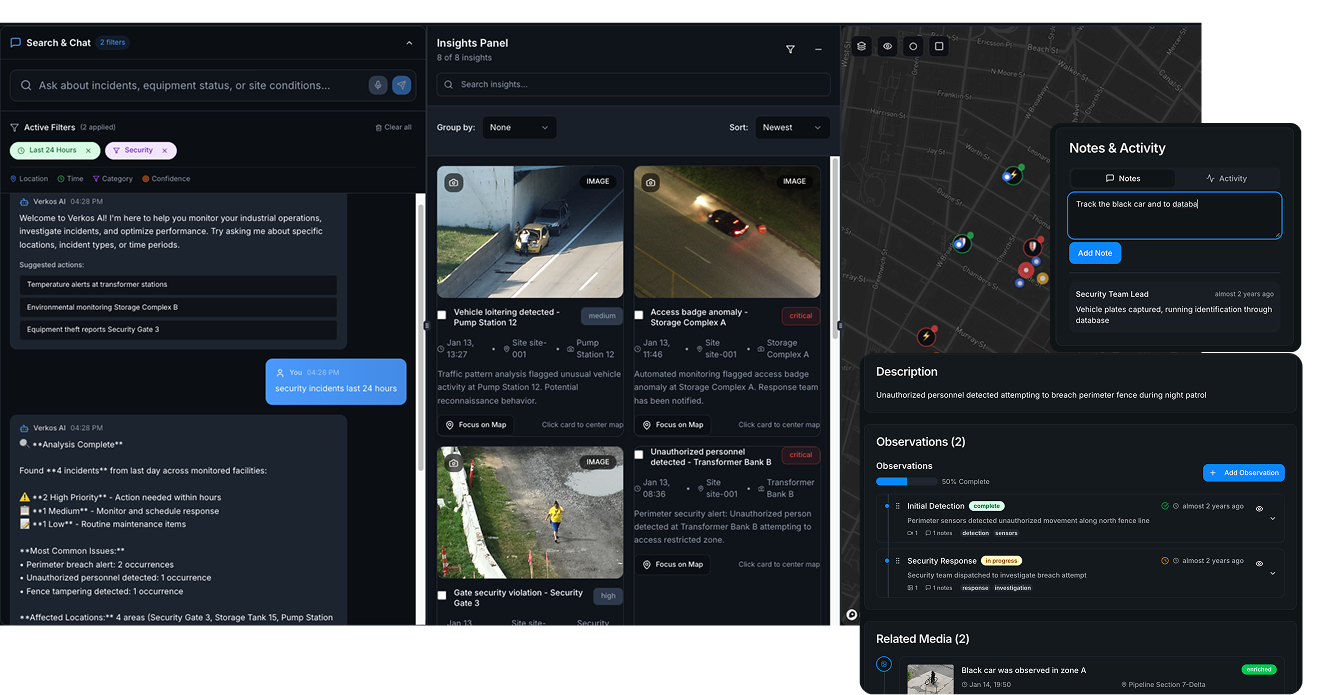
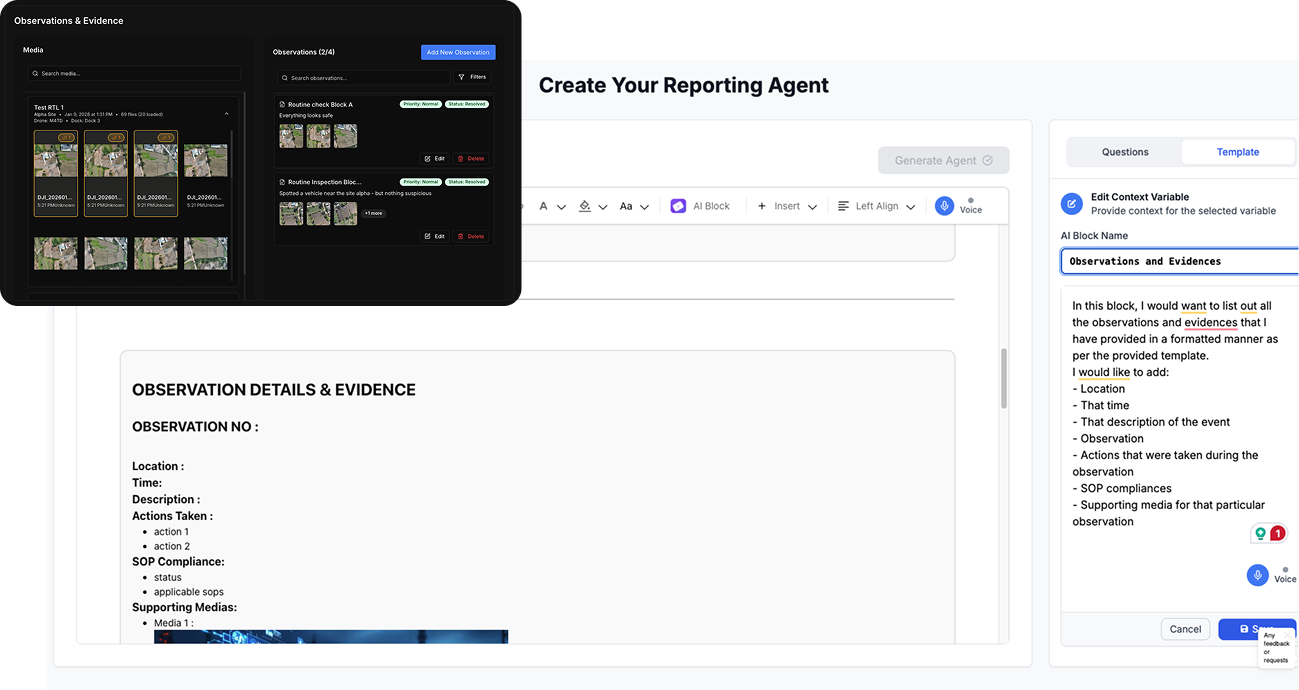
Evidence and reporting
Where Security Service Providers Deploy Aerial Intelligence

Construction and Infrastructure

Logistics, Warehousing, and Open Yards

Industrial and Manufacturing

Energy and Utilities

Commercial Campuses
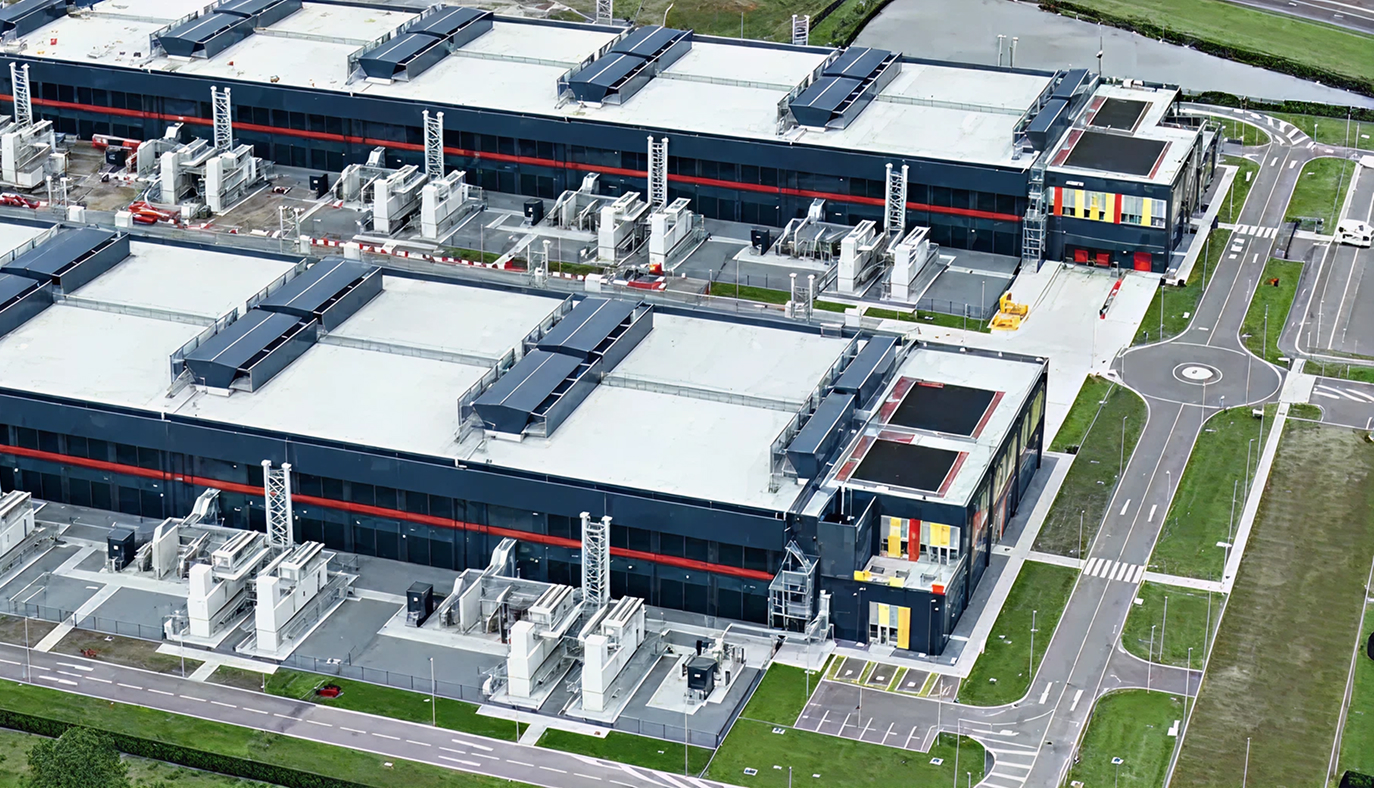
Data Centers and Critical Sites

Gregory Neyland

Tyron Mangakahia
AI Agents For Enterprise and Managed Security Environments

After Hours Activity Detection
After Hours Activity Detection
Detects any person or vehicle activity outside defined operating schedules and triggers an incident automatically.

Restricted Zone Violation Detector
Restricted Zone Violation Detector
Flags movement inside customer-defined no-access or high-risk zones with verified alerts.

Perimeter Breach Detector
Perimeter Breach Detector
Detects boundary crossings at fence lines or virtual perimeters and captures entry paths as evidence.

Loitering Behavior Monitor
Loitering Behavior Monitor
Identifies people or vehicles remaining in sensitive areas beyond acceptable time thresholds.

Gate Tailgating Detector
Gate Tailgating Detector
Detects unauthorized follow-through entries at controlled gates and access points.

Coordinated Intrusion Detector
Coordinated Intrusion Detector
Identifies coordinated behavior across multiple individuals such as lookout-and-entry patterns.
Designed to Work With Your Deployment Stack
Docks and Drones

Loudspeaker

Spotlight
Drone Autonomy Software Platform
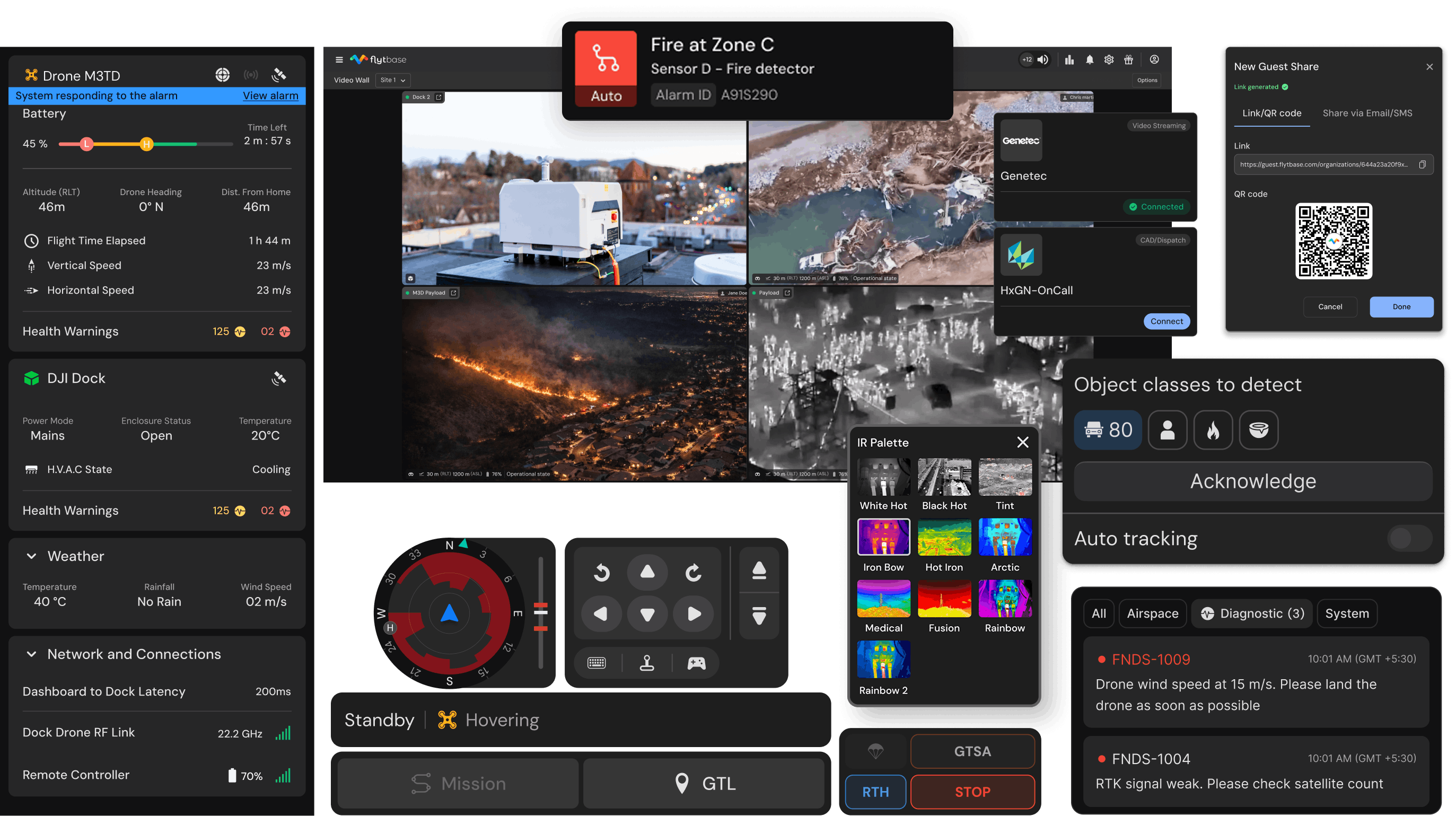
Apps
Genetec
HxGN OnCall
Milestone
License Plate Detection
ShotSpotter
Flight Safety Integration
AVSS Parachutes
Senhive
Dedrone
Enterprise Security Standards
.png)
Let's Build A Deployment Plan
Tell us about your sites, security model, and operational constraints. We will design a pilot deployment, validate response times and cost impact, and define a clear path to scale across enterprise sites or managed security portfolios.




